I have multiple things running through a reverse proxy and I’ve never had trouble accessing them until now. The two hospitals are part of the same company, so their network setup is probably identical.
Curiously, it’s not that the sites can’t be found, but instead my browser complains that it’s not secure.
So I don’t think it’s a DNS problem, but I wonder what the hospital is doing to the data.
All I could come up with in my research is this article about various methods of intercepting traffic. https://blog.cloudflare.com/performing-preventing-ssl-stripping-a-plain-english-primer/
Since my domain name is one that requires https (.app), the browser doesn’t allow me to bypass the warning.
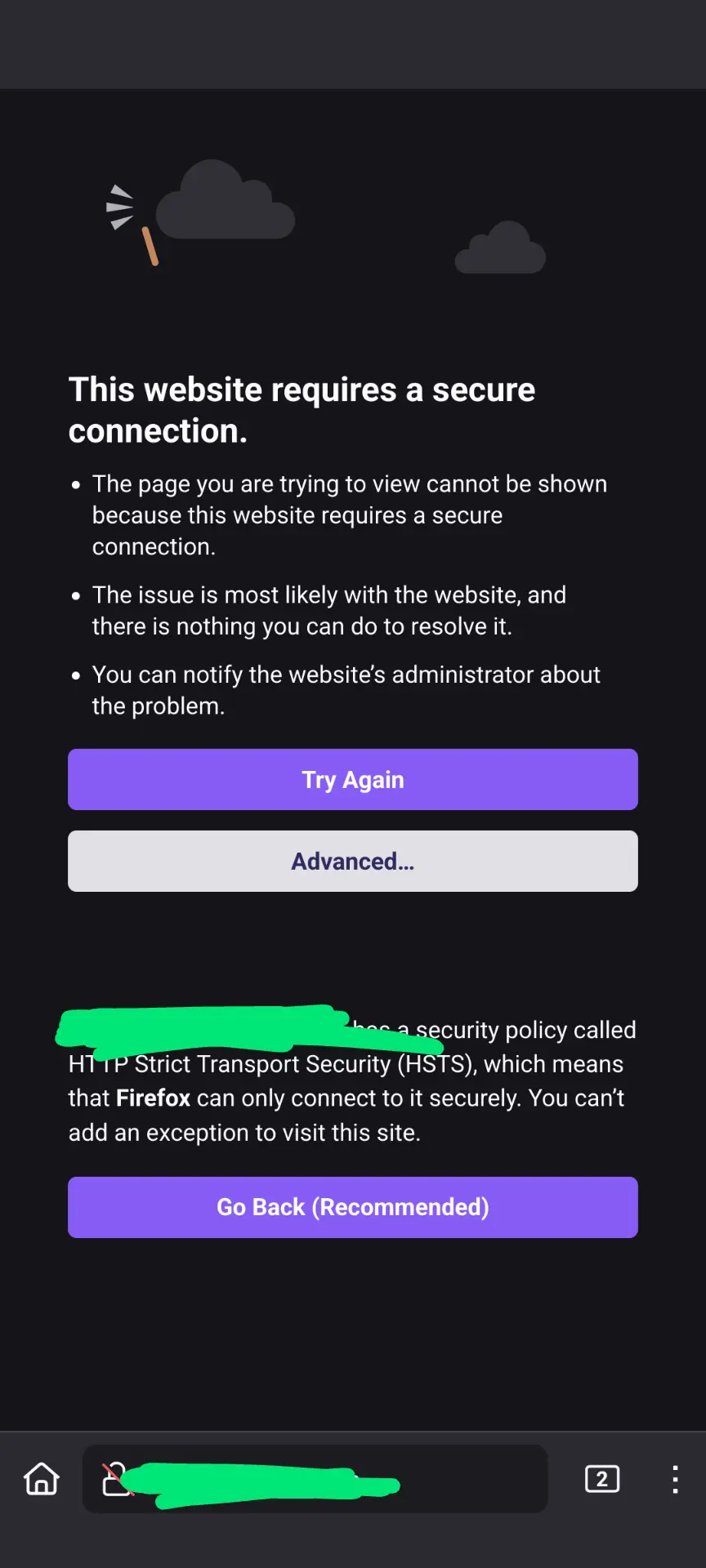
Is this just some sort of super strict security rules at the hospital? I doubt they’re doing anything malicious, but it makes me wonder.
Thanks!
Also, if you know of any good networking Lemmy communities, feel free to share them.


They may block IP addresses associated with consumer ISPs. Assuming that’s the case, I would guess you’re seeing that as an HSTS/TLS error because their network is trying to trick your browser into redirecting to/displaying an error page hosted by some part of their network.
Once a browser has seen an HSTS flag it will never attempt a non-TLS connection to that site (unless it successfully makes a TLS connection and the flag is gone).
This error is caused by a bad certificate. It can show up if your certificate expired, for instance. It’s confusing that the HSTS error takes precedence, I think the bad certificate should take precedence but there you have it.
My money is on the hospital trying to use TLS stripping.